As I detailed in my last post, file sharing/syncing is quickly transforming how, where and when we work by making our apps and data available and usable on any Internet-connected device. Even if your organization doesn’t have an enterprise-grade file sharing/syncing capability in place, odds are your employees have attempted to make their lives easier by implementing their own consumer-grade alternatives.
That’s a good thing insofar as it reveals genuine demand — but also not so good, mainly because of the security risks inherent in consumer-grade services. So the trick is to find a file sharing/syncing solution that includes several essential characteristics not found in far riskier consumer-grade alternatives.
A new kind of file sharing/syncing platform
In addition to easy file sharing and accessibility, an enterprise-grade file sharing/syncing platform should separate its filesharing application plane from its underlying storage plane. This provides a global namespace into all company data/apps that a user has permission to access, resulting in a single view of corporate files.
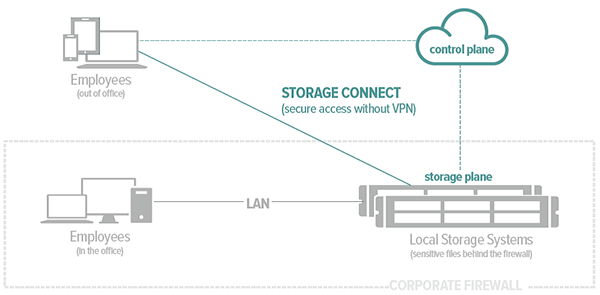
Thus your employees can access files through a single unified namespace regardless of where files are located while your IT staff can maintain high levels of permission security by centrally managing and authenticating users through your existing corporate identity management system.
Protecting sensitive data “in place”
What’s more, unlike cloud-only file sharing/syncing solutions that force you to move huge amounts of data into cloud environments, you can leverage your existing data storage environment and enable access and sharing/syncing of “in place” data. Look for an enterprise-grade file sharing/syncing solution that will perform with any existing storage platform and file access protocol without requiring additional proprietary file system protocols.
This kind of file sharing/syncing platform is essential if you have data that’s just too sensitive for the cloud, since it gives you the ability to provide mobile and remote VPN-less access to any local storage without files or file metadata passing through any cloud environment. So your data is appropriately accessible while remaining behind the corporate firewall where you can keep it secure from privacy risks and government monitoring.
With such an architecture, your IT staff can maintain comprehensive administrative control (e.g., user access/authentication, mobile data management, encryption, audit reporting and industry compliance) while addressing all of the use cases your business is likely to encounter, from local desktop/laptop data backup, access and sharing all the way to backing up data residing in on-premise storage devices, powering cross-office collaboration and ensuring business continuity when an Internet connection is unavailable.
Free at last …
A file-sharing/syncing solution based on an architecture that uses a unified namespace for all files, regardless of data sensitivity, permits your employees to use one IT-sanctioned file sharing service rather than adopting rogue consumer-grade cloud solutions that can lead to data leaks, privacy breaches and security risks you cannot afford.
