
These days, your end-users have usually become the weakest link in your data security chain, so attacks are shifting from the server side to the client side, notably to mobile devices like smartphones.
According to one Symantec report , 2010 saw a 93% increase in the volume of Web-based attacks — and during a single three-month stretch in 2010, 65% of the malicious URLs Symantec observed on social networks were shortened URLs .
Even mobile device users abiding by company acceptable-use policies are vulnerable to non-technical attacks like ‘shoulder-surfing’, thanks to highly visible screens that enable crooks to observe log-in details during the authentication process.
The pitfalls for end-users extend well beyond their smartphones and tablets. Take, for instance, search engine poisoning, which has been described as an extreme form of black hat search engine optimization. In search engine poisoning, the bad guys exploit popular search terms (e.g.,’ death of Osama bin Laden’ or ’Haiti earthquake’) by flooding search results with links to bait pages that redirect unwary users multiple times, generally until they land at an irrelevant page that serves as a malware vector.
These sites, which may be legitimate but compromised, are part of extensive malware delivery networks and are optimized so they rank high in search results — and their creators are becoming adept at hiding their malicious payloads from search engine crawlers by presenting a clean Web page.
Data loss prevention solutions can help. DLP discovers, monitors, controls, and secures sensitive data (in use and at rest) on your network, on employee desktops or laptops, and/or data residing on end-user systems and network servers.
Also, you need to train your employees to recognize various methods of social engineering and their vectors, such as clicking on email attachments from unknown senders or installing unfamiliar smartphone apps.
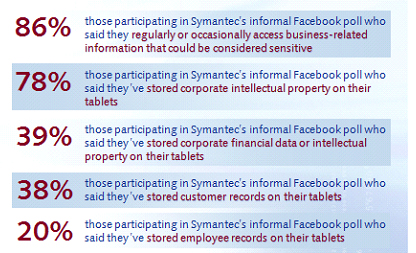
Infographic source: Survey Finds an Alarming Gap Between Tablet Usage and Security, September 29, 2011
