
The ever-richer user information on social media presents an irresistible opportunity for ‘fraudsters.’ Because it’s so easy to research a target online, attackers have developed very effective masquerading and social engineering tactics that can fool even the most sophisticated users.
Spear phishing, for instance, involves quite plausible deceptions based on publicly available information from company websites, social networks, and other sources. Emails sent to the target seem legitimate because they include this information — but the emails also include malicious files or links to malicious websites, and if the target is successfully duped, attackers potentially gain access to sensitive corporate data.
Attackers taking advantage of still-evolving social media to defraud people and organizations will generate serious compliance challenges for businesses that function under regulatory and compliance mandates.
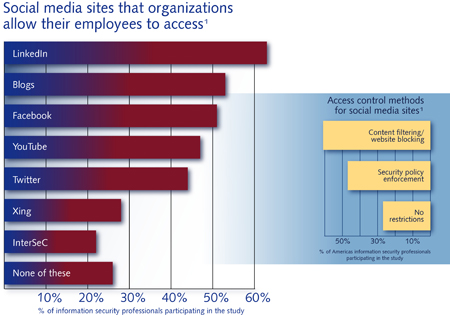
You can go a long way to protecting your business’s IT infrastructure by developing and enforcing a clear, concise security policy that meets your organization’s compliance requirements — and includes social media dos and don’ts.
Infographic source: The 2011 (ISC)2 Global Information Security Workforce Study, Frost & Sullivan
