Consider: Last year, according to Verizon , 54% of data breaches began as attacks on web applications, and for years one type of attack — SQL injection — has been the means by which 83% of stolen records were extracted. Meanwhile, says Gartner , 25% of all DDOS attacks this year will be application-based, and an increasing portion of these attacks may actually be diversions in which the bad guys use remotely accessible malware to target user accounts (for personal data or, in the case of financial institutions, for money).
Equal opportunity risks proliferate for large and small organizations alike in key application-heavy arenas:
Big, bad browser plug-ins.
Today’s web clients, for instance, are more than mere browsers. They act as platforms, complete with infrastructure, utilities, and plug-ins that provide extensibility but also now present plenty of vulnerability, since attackers create exploit kits disguised as browser plug-ins. Over the last year, attackers have frequently targeted applications like Adobe Acrobat Reader, Adobe Flash Player, and Microsoft Office as well as Internet Explorer and Oracle Java.
Smartphones, not-so-smart users.
The latest crop of sleek mobile devices might be cool — but not so much if you worry about security. Mobile devices function like rogue endpoints: These troves of personal and corporate data can be anywhere, they’re routinely connected to unknown networks, too often the device OSs are unpatched, while app encryption is incorrectly implemented and device users’ notoriously poor password and click-on-anything habits continue.
Clouding over the details.
When it comes to cloud apps, security issues tend to be spawned from policy and procedure problems rather than technical difficulties. The comparatively well-defined security responsibilities typical in a traditional application environment don’t always make the transition to a cloud architecture, creating cracks through which attackers can creep unless cloud security roles and policy are documented and enforced.
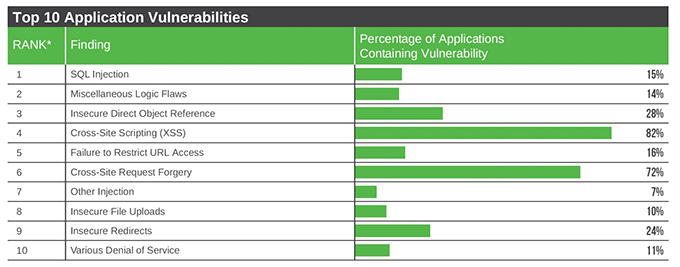
Source: Trustwave 2013 Global Security Report, http://www2.trustwave.com/rs/trustwave/images/2013-Global-Security-Report.pdf
The simple truth is that if your enterprise uses the Internet to conduct business of any sort, it faces heightened risk of attack and breach. Because of the variety of attack vectors and the easy-to-use attack toolkits now available, sooner or later, your organization will be attacked.
Countermeasures — many of them simple and inexpensive to implement — abound. But unless you can afford a platoon of security specialists, you’ll have a hard time keeping up with the constant churn in threat vectors. Fortunately, you can get affordable help from dedicated security services experts who understand the threats you face and can craft security solutions that meet your unique requirements.
