
These days, two-thirds of all applications rely on open-source components. While open source has many virtues, it also has a key vice: once an open source component is integrated into an application, that app inherits any vulnerabilities it contains.
Further, whenever that application is referenced by other software, the inheritance of the initial vulnerability persists. The 2014 Heartbleed bug occurred in this way, and some version of this issue is likely to keep happening because most vendors don’t list all the third-party components their software relies on.
How many of your web and mobile apps are compromised?
Since Heartbleed, plenty of open source application security issues have been tamped down, but vulnerabilities remain widespread — especially among web and mobile apps. Indeed, few organizations can say their web apps have not been compromised . And such compromises cost plenty:
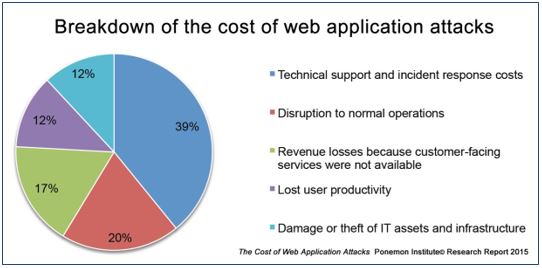
And it isn’t hard to see why: fewer than half of all web apps are tested for vulnerabilities , and it typically takes days to weeks to fix a compromised web application .
Mobile apps, too, are vulnerable. For instance, more than 5 billion downloaded Android apps are susceptible to remote attacks. Problematically, attackers now work simple modifications into their code, so the hash is unique but their malware exhibits the same mal-behavior.
Keeping your apps secure
Here’s three of the most important things you can do to maintain application security:
- Involve your security team early on. When it comes to creating applications, bring your security team on board right at the beginning so they can influence your app language and methodology choices.
Consider, for example, that web apps written in web scripting languages are more vulnerable to SQL injection and cross-site scripting than apps written in .NET or Java. And mobile apps have notably high rates of cryptographic issues. - Scan your app builds. Repeated scans (static and dynamic application analysis) are an essential part of a secure software development lifecycle because they go a long way to mitigating known vulnerabilities.
- Monitor your networks, systems, and apps. Regardless of the applications you build or use, you need to monitor them and the systems, networks, and data they interact with so you can spot irregularities — and particularly so you can identify when threat actors are doing reconnaissance on your environment in preparation for an attack.
In today’s increasingly mobile world, attacks can involve various (and multiple) layers of infrastructure — firmware and application layers on your host processors, smartphone apps, or cloud services — as well as a range of propagation vectors, such as exploiting network and host processor communication layer vulnerabilities, compromising update files, etc.
Oh, and I have a #4: Don’t be daunted.
If you lack the resources in-house to sustain application security or a secure software development lifecycle, get help from an experienced technology security expert who can assess your needs (including a web app security scan ), provide secure application development and support services , and put together an affordable plan customized to your organization’s needs .
